In place of these websites, you can find 1 System You will be observing much, considerably more of: Reddit. In accordance with Semrush, Reddit noticed a surge that amounted to the 126% development in traffic from Google Look for.
The actual written content in the video ends up being absolutely unrelated, a Rickroll, offensive, or just on-display textual content of a website link to the site remaining promoted.[32] In some cases, the connection in concern may bring on an internet study web-site, a password-secured archive file with Guidance resulting in the aforementioned study (even though the study, as well as the archive file by itself, is worthless and isn't going to have the file in issue in any way), or in Severe conditions, malware.[33] Many others may well add video clips presented in an infomercial-like format offering their item which characteristic actors and paid out recommendations, while the promoted service or product is of doubtful top quality and would possible not pass the scrutiny of a expectations and practices Section in a tv station or cable community. VoIP Spam[edit]
But in addition to that, a third party “authority” metric is not really anything at all I have ever applied and will never use. Lots of SEOs with longtime expertise don’t use All those metrics.
Do a search for the topic of curiosity, e.g., "M Concept"; click the envelope icon during the sidebar of the search engine results site; enter your e mail tackle, and click "Produce warn". We will then periodically e-mail you freshly released papers that match your search conditions.
Additionally, it involves citations for conditions cited by indexed thoughts or journal articles which lets you locate influential situations (generally more mature or international) which aren't yet online or publicly readily available.
This perform has actually been Component of Google’s DNA considering the fact that our founding in 1998. Component of our lifestyle just after we’ve hit a milestone is to talk to ourselves “what far more can we do?”, and we're applying that to our weather goals.
International Convention on Computer software Engineering: Program Engineering in Follow (ICSE-SEIP)(2024) (to seem) Preview Preview summary In machine learning packages, it is commonly cumbersome to annotate the size of shapes of various tensors that get produced all through execution. We current a dynamic likely tensor form inference Examination that annotates the scale of shapes of tensor expressions with symbolic dimension values.
Transaction Charge: The incremental cost of making contact with Each individual more recipient the moment a means of spamming is created, multiplied by the number of recipients (see CAPTCHA for a method of raising transaction charges).
As soon as you access the right webform, you should include things like the specific URL(s) from the material you wish to report, rather than the website link to the web site’s dwelling webpage. Find out how to find the proper URL.
If your site makes use of systems that engines like google have problem accessing, like JavaScript or images, see our recommendations for producing that information accessible to search engines like yahoo and end users devoid of cloaking. If a web page is hacked, it's not unusual to the hacker to implement cloaking to help make the hack harder for the site operator to detect.
Even a Erroneous guess might allow you to don't forget the proper facts Once you Google. And who is aware, maybe the arcana will include on your reservoir of data and will in the end allow you to study a little something considerably more worthwhile.
Mueller answered that it’s not required to do anything about “spammy backlinks” due to the fact Google ignores them. He didn’t even advise utilizing the Disavow Instrument, a Software that tells Google to ignore certain inbound links that a publisher is accountable for.
WACV 2024(2024) Preview Preview summary Deep networks have a tendency to learn spurious aspect-label correlations in true-earth supervised Studying jobs. This vulnerability is aggravated in distillation, exactly where a (scholar) model can have considerably less representational potential in comparison to the corresponding Instructor product. Generally, knowledge of certain trouble attributes is used to reweight cases & rebalance the training procedure. We suggest a novel early readout mechanism whereby we try to predict the label using representations from previously community layers. We demonstrate that these early readouts quickly establish problem scenarios or groups in the shape of assured, incorrect predictions.
When analyzing if a redirect is sneaky, report the articles by google take into account if the redirect is meant to deceive both the users or search engines like google and yahoo. Find out more regarding how to correctly hire redirects on your web site. Site track record abuse
 Emilio Estevez Then & Now!
Emilio Estevez Then & Now! Scott Baio Then & Now!
Scott Baio Then & Now!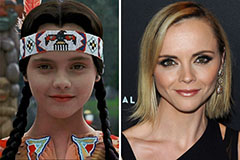 Christina Ricci Then & Now!
Christina Ricci Then & Now!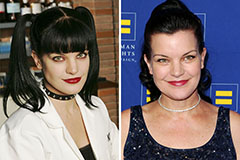 Pauley Perrette Then & Now!
Pauley Perrette Then & Now! Lucy Lawless Then & Now!
Lucy Lawless Then & Now!